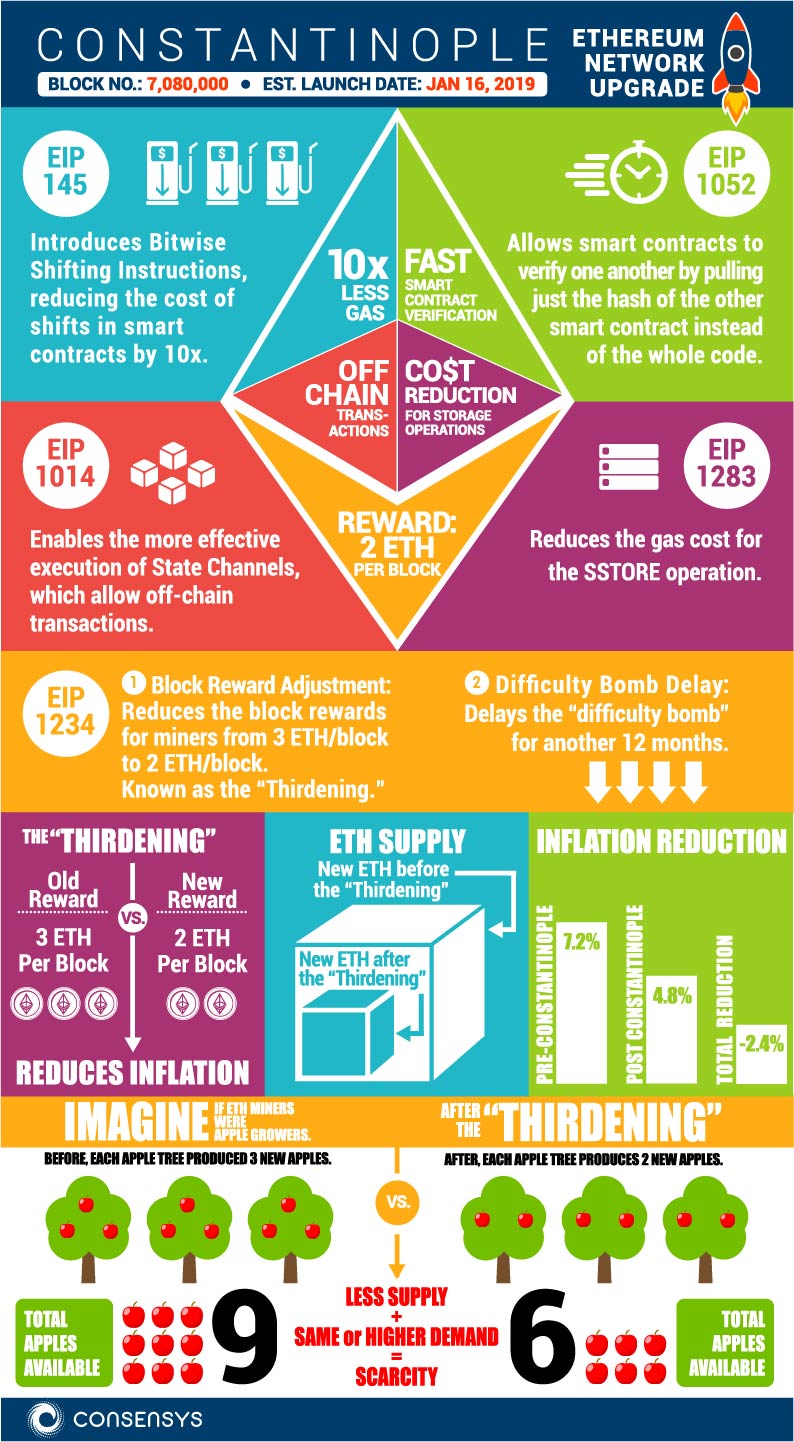
The long-awaited Constantinople fork of the Ethereum network has been delayed due to potential security issues identified by ChainSecurity. An innovation of the Constantinople update was the introduction of cheaper gas cost for certain SSTORE operations. The Swiss blockchain security company warned that this would enable reentrancy attacks.
Don’t Worry – Update and You Won’t Be Sorry
Following ChainSecurity’s revelations, key stakeholders within the Ethereum community decided to postpone the Constantinople fork, initially scheduled to launch January 16, 2019.
[SECURITY ALERT] #Constantinople upgrade is temporarily postponed out of caution following a consensus decision by #Ethereum developers, security professionals and other community members. More information and instructions are below. https://t.co/p2znO8HGxf
— Ethereum Foundation (@ethereum) January 15, 2019
This means anyone running a node – node operators, exchanges, miners, wallet services – has to update a new version of Geth or Parity before block 7,080,000.
Block 7,080,000 will occur at approximately 8:00pm PT/January 16, 4:00am GMT/January 17. Update your Geth and/or Parity instances to the updated versions using the links below:
Geth
- Upgrade to 1.8.21, OR
- Downgrade to Geth 1.8.19, OR
- Remain on 1.8.20, but use the switch ‘–override.constantinople=9999999’ to postpone the Constantinople fork indefinitely.
Parity Ethereum
- Upgrade to Parity Ethereum 2.2.7-stable (recommended)
- Upgrade to Parity Ethereum 2.3.0-beta
- Downgrade to Parity Ethereum 2.2.4-beta (not recommended)
If you are simply interacting with Ethereum (you do not run a node), you don’t need to do anything!
Ledger, Trezor, Safe-T, Parity Signer, WallEth, Paper Wallets, MyCrypto, MyEtherWallet and other users or token holders that do not participate in the network by syncing and running a node can remain calm. The change that would introduce this potential vulnerability won’t be enabled.
Snapshot of Ethereum Constantinople Update. Image Source: Consensys
Vulnerability of Smart Contract
The analysis by ChainSecurity dives deep into the potential risk of the Constantinople fork and how smart contracts can be checked for their vulnerability.
EIP-1283 introduces cheaper gas cost for SSTORE operations. But their findings show that some smart contracts already on the chain may utilise code patterns that would make them vulnerable to a reentrancy attack after the Constantinople upgrade took place.
Contracts that increase their probability to being vulnerable are contracts that utilise a transfer() or send() function followed by a state-changing operation. Take for example a contract where two parties jointly receive funds, make a decision on how to split these funds and trigger a payout of those funds.
Don’t Jump the Gun – Wait and See
There is a non-zero risk that some contracts could be affected, according to ChainSecurity.
Out of an abundance of caution, stakeholders of the Ethereum network decided to delay the update. There was not enough time to clear away all security risks before the planned fork on January 16, 2019.
Security researchers, Ethereum client developers, smart contract owners and developers, wallet providers, node operators, Dapp developers and media were involved in the discussion leading up to the decision.
If you want to stay up to date on the latest Constantinople and Parity Ethereum developments, follow @ParityTech on twitter or check out the Ethereum Blog.