St Francis Xavier University in Canada recently came under attack by hackers, forcing a week-long network shutdown on campus.
The hack began on November 1st, according to broadcaster GlobalNews.ca. Malware took over the network as so-called ‘cryptojackers’ used the school’s electricity and hardware to illegally mine cryptocurrencies.
By Nov. 4th most services were up and running again, as university staff took to Twitter with updates.
The systems restart process continues and is proceeding well. Timing of having the systems completely operational is still being determined, however, we remain committed to keeping the campus community updated as we continue to work toward restoring all systems. @TheUOfficial
— StFX University (@stfxuniversity) November 2, 2018
In a statement to press, the university acknowledged the severity of the attack and outlined their IT Services (ITS) response.
“On Thursday, ITS, in consultation with security specialists, purposefully disabled all network systems in response to what we learned to be to be an automated attack on our systems known as cryptocoin mining.”
Fortunately the cryptojackers, who remain at large, did not access or steal any sensitive data. It’s not known if St Francis Xavier University will pursue the matter with a criminal investigation.
The Who, What and Why of Cryptojacking
Cryptojacking is an emerging type of hack, with a rate of incidence that coincides with the growing popularity of cryptocurrencies.
Cybersecurity firm Norton describes cryptojacking as “the unauthorized use of a computer, tablet, mobile phone, or connected home device by cybercriminals to mine for cryptocurrency.”
The hacking operation is done remotely, and any mined coins are sent to the cryptojacker’s wallet. While the victim incurs the cost of electricity and hardware, the hacker reaps the reward.
With the chance to earn thousands of dollars in bitcoins or altcoins, cryptojacking is a lucrative scam for program-savvy criminals. It’s no wonder that the number of attacks is increasing daily.
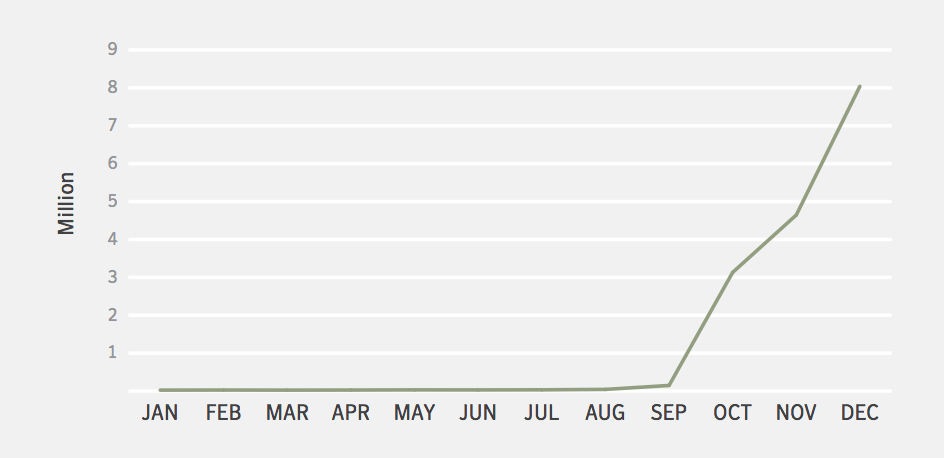
Symantec’s Internet Security Threat Report reveals a recent boom in cryptojacking operations from 2017 onwards.
The chart below shows a very low rate of cryptojacking activity until September 2017 when cryptocurrency trading went mainstream. From then on, the number of incidents rose dramatically reaching 8 million in December alone.
Most computers are extremely vulnerable to cryptojacking, even Macs despite their secure reputation. In the chart below, Symantec found the number of Apple products facing attack in 2017 closely mirrored the industry average.

Unfortunately, as the number of cryptojacker attacks increase so does their sophistication.
CCN.com reported last month that hackers are using fake flash software updates to hide cryptocurrency mining malware on Windows computers. Cryptojackers have employed this trojan horse strategy with fake Adobe updates as well.
The epidemic of cryptojacker activity shows no sign of slowing, and prevention is more important than ever.
Building a Prevention Strategy
Unsurprisingly, Norton recommends installing a strong security system on your computer. But there are there are ways to reduce the risk of cryptojacking at no cost as well.
Be careful when downloading software or documents from the internet, even if they come from a trusted source. Cryptojackers count on a user’s ignorance to worm their way into personal computers, so beat them at their own game.
Consider installing simple ad-blockers — they screen out dubious requests and fewer ads will clutter your screen!
At the end of the day, do your research and education yourself about the threat and the risks. To learn more, check out Bitcoin Australia’s educational guide here.