What is a Cryptolocker?
A Cryptolocker is a high-level computer virus, usually circulated in the form of an attachment, disguised to look like an Auspost email notification or invoice such as an energy bill. Opening or downloading the attachment will lead to you having all your data encrypted and leaving you 3 days to pay a ransom or suffer complete loss of all your files.
At times hiding in a link sent to you on Facebook, Skype, etc. If you get a request from a friend, family member or work colleague to pay money or check an attachment, always double check via a phone call or SMS.
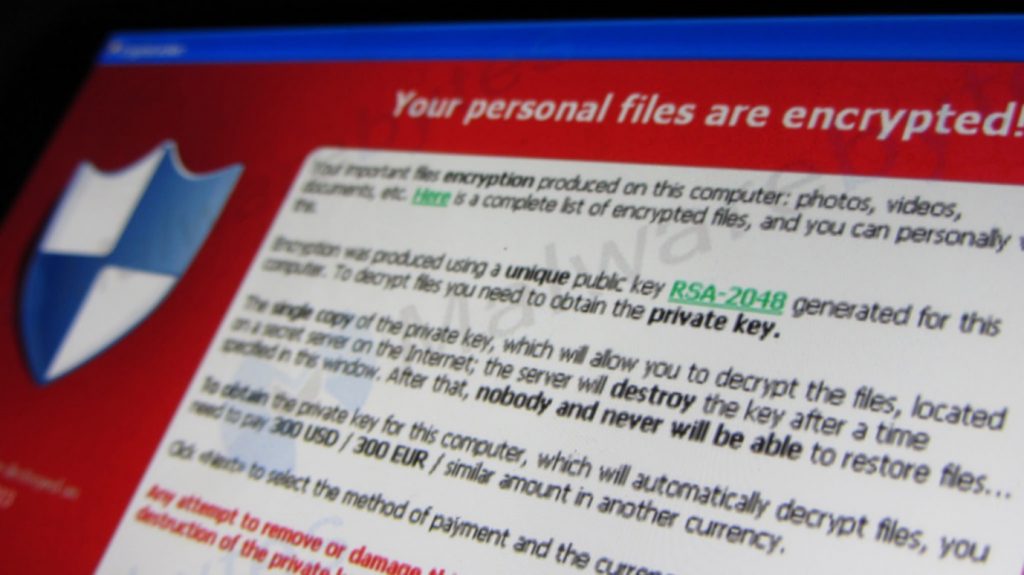
Cryptolockers are LOUD. Once you have contracted the virus and it has manifested itself, you will definitely know. A popup screen will appear telling you that your machine has been locked up and all your files encrypted (see image below). The hacker will usually give you countdown clock, to increase panic, every tick dragging you closer to hard-drive wipeout.
All data is worth something to someone and Cryptolockers are all about monetising that data. It has become one of the most highly sophisticated and profitable viruses to date, making over 1 Billion dollars in 2016 alone. Once the virus is contracted, it can cost anywhere between $1,500 – $15,000 to retrieve your data.
But all is not lost, there are prevention methods that when effectively put in-to place allow us to be evasive and able to recognise the indicators of this malicious malware.
How to effectively prevent Cryptolockers?
There are methods that can be taken to reduce the risk and overall damage done by the whole process, the first and foremost… Prevention is the best cure!
- Backup, backup and more backup! Purchasing an external hard-drive is an increasingly affordable way to mitigate this virus threat. Importantly, store these backups offline, there have been reports of the virus spreading to online backups.
- Prevent what’s preventable, limiting the amount of files a user account has access to, can limit the scope of what can be encrypted by an intruding infection.
- Personalising your anti-spam settings in your webmail server to block attachments such as .exe .vbs .scr .7z; webmail services such as google mail or Office365 can be configured to prevent these types of attachments from showing up in your mailbox.
- Refrain from opening any attachments that look suspicious, the emails may say that that they are from a delivery service, e-commerce resource, acquaintance, law enforcement or even banking institution, e.g. Auspost, e-gas or any major Australian company.
- Generally just think twice before clicking on any hyperlink or attachment that is posted to you, even over social media platforms such as Twitter or Facebook, there are ways for the attacks to be deployed through direct messaging. If in doubt, call the person in question to confirm the contents of the message.
- Keeping your operating system, antivirus, browsers, Adobe-flash player, Java and other software up to date is vital as it will allow for less overall exploits when you are running up-to-date software.
- File sharing is an issue as when the infection hits, file sharing will allow the infection to spread into the local area network spilling into neighbouring computers.
- If you were to recognise the Cryptolocker virus on your system, instantly disconnect yourself from the internet before it has the chance to establish a connection with its Command and Control server and thus cannot complete the encryption routine.
- Inform your colleagues and friends of the risks associated, all it can take is one employee to take down an entire company’s data, the cost of prevention is far less than the ransom!
Things to Remember
- For the most part be careful who you are giving your emails out to in general, in the sense that some companies may be handing your email data out to 3rd parties. If you don’t feel that you need to sign up to a subscription service then don’t!
- Downloading any movies off websites or torrent services may have Cryptolockers embedded.
- Invest in adequate anti-virus blocking services, such as Norton or Kaspersky as a prevention method to have early warnings on any malicious software/emails/downloads.
- The old tale that Mac’s cannot get viruses is well and truly beyond a myth, all Mac users need to be mindful and aware that their machines are just as vulnerable as any piece of technology to this day including iPhones and neighbouring mobile devices.
Best course of action upon infection
- The appropriate thing to do is to contact an experienced IT professional. The Cryptolocker virus is always evolving, it can be important that an IT professional diagnoses the specific virus you have. Do not try to do this yourself, the virus tries to impersonate other viruses to obscure the method of removal without paying the ransom.
- If the IT company has dealt with the virus before, there may be a chance of removing the virus without paying the ransom. We recommend Pclink.com.au (1300 500 400).
- If the IT company cannot remove the virus without paying the ransom, you may have to decide whether your data is worth the price. Note: Please know that paying the ransom only ever perpetuates the success of the virus, please consider this carefully, paying the ransom increases the likelihood of other people getting the virus. In many cases, paying the ransom will lead to you being re-targeted.
- The final choice is to pay the ransom, generally this would require you to purchase bitcoins, feel free to call our staff at btcuks1.wpengine.com and we will be happy to assist you with your problem. Note: We will only ever sell bitcoins to a customer who is a victim of ransomware once they have spoken to an IT professional and it is in their professional opinion that this is the last resort.
We hope this helps you inform yourself about the latest and deadliest computer virus so far, remember, prevention is the best cure!
It may be worth calling your IT professional today and seeing how to upgrade and fine tune your systems to prevent this deadly threat before it hits you!